Security and compliance, built in.
Everything in Conversion is designed with security, privacy, and compliance in mind, from how access is managed to how data is logged, audited, and shared.

















Enterprise-grade security
Built with security-first infrastructure and controls, aligned with modern SaaS best practices.





Conversion has completed a SOC 2 Type II audit. Reports available upon request.





Committed to compliance with the EU General Data Protection Regulation (GDPR).





Restrict access to system-level permissions and sensitive actions.


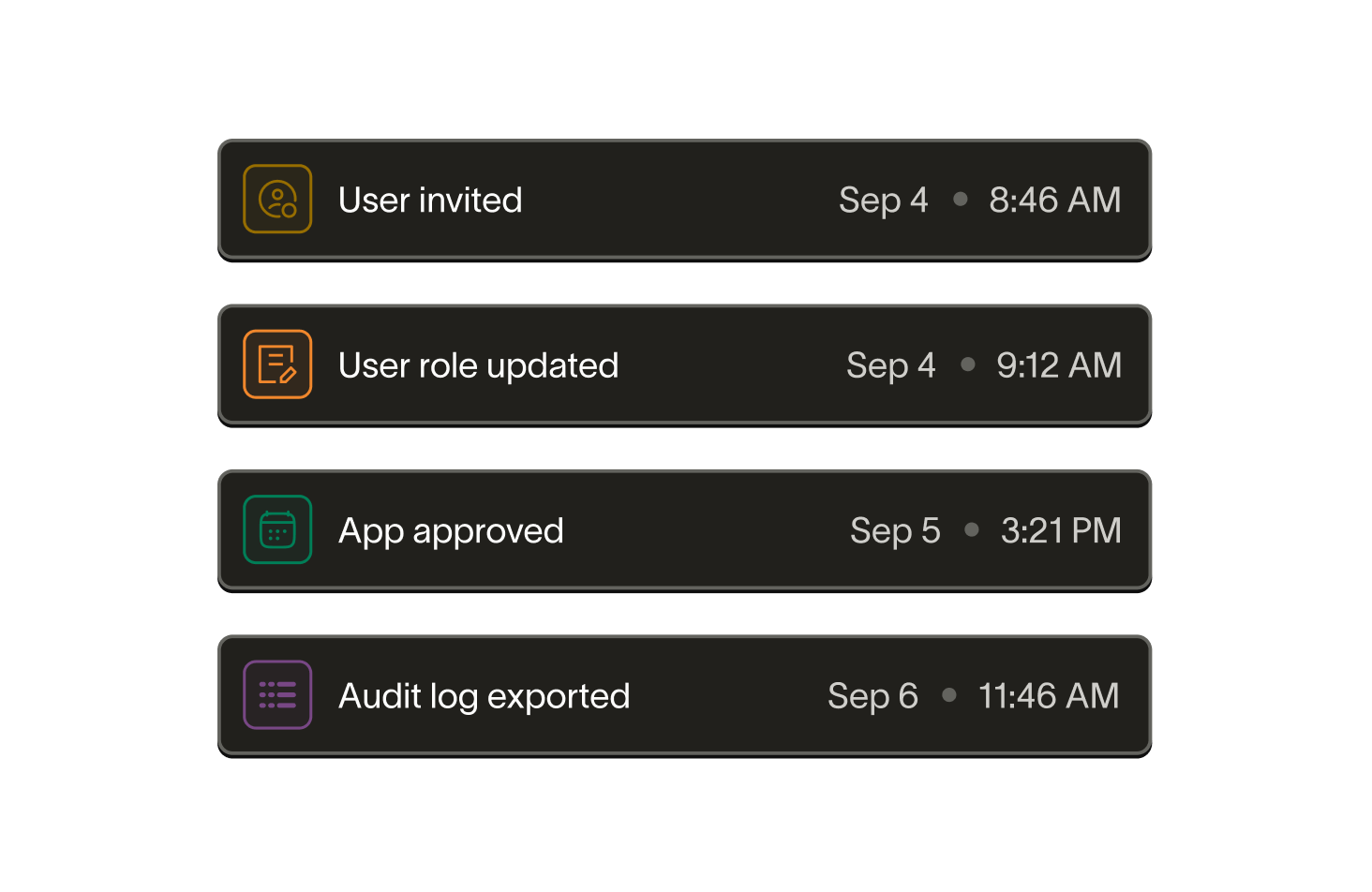


Comprehensive audit logs track user activity and data sent to connected third-party applications.





Control which third-party applications can access your Conversion workspace.





Authenticate via any SAML-compatible identity provider.





Provision and deprovision users automatically through your identity provider.





Support for passkeys, domain claiming, and login method restrictions.





Works with Google, Entra, Okta, OneLogin, LastPass, Auth0, Bitium, and more.
Frequently Asked Questions
Experience how an AI-native platform approaches security, privacy, and data handling differently from legacy marketing automation.

You can find it here!
You can read more about our processing guidelines through our Data Processing Agreement.
You can request relevant security documentation through our Trust Center.
No we do not. We work with trusted third party model providers that explicitly prohibit model training on customer data.
We communicate service-impacting outages via our status page.
We force HTTPS on all connections and encrypt data in-transit with TLS 1.2. All data at-rest is secured using AES 256-bit encryption.




.png)
